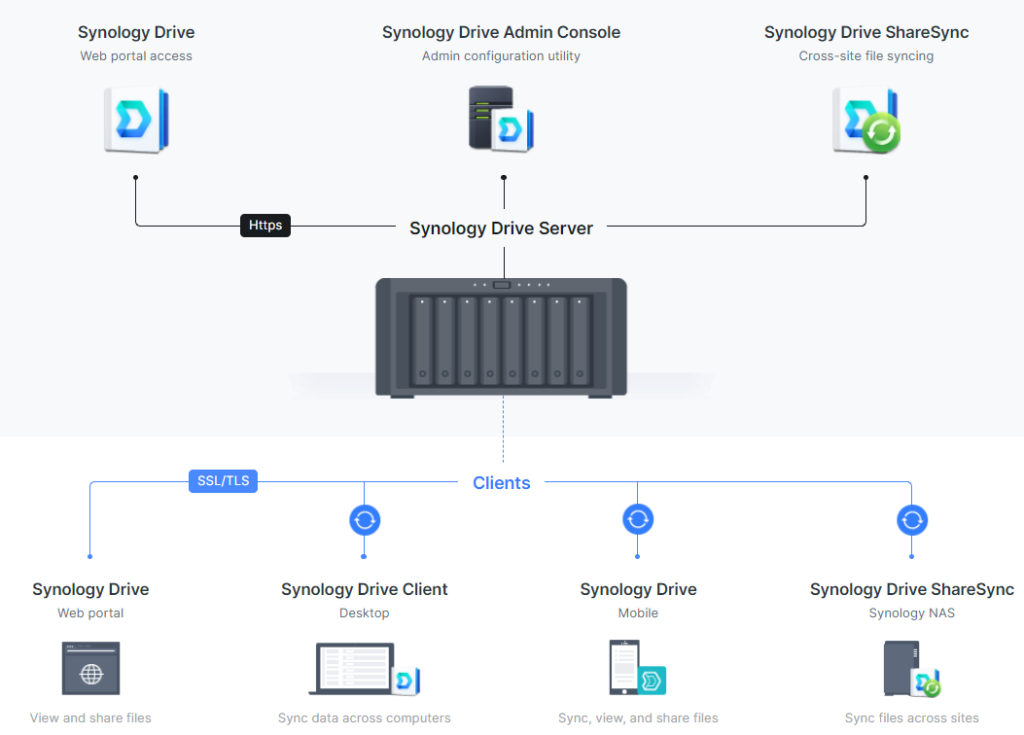
Security Considerations When Accessing a NAS Remotely
Remote access to a NAS (Network Attached Storage) brings convenience and flexibility, but it also introduces security risks. Here are some important considerations:
1. Authentication and Access Control
Ensure strong authentication mechanisms are in place, such as using complex passwords, implementing two-factor authentication, or using digital certificates. Restrict access to only authorized users, and regularly review and update access permissions.
2. Secure Communication
Encrypt the communication between the remote client and the NAS using protocols such as SSL/TLS. This prevents eavesdropping and protects data confidentiality.
3. Firewall and Port Management
Configure the firewall to allow only necessary ports for remote access to the NAS. Limit access to specific IP addresses or ranges, and regularly monitor for any unauthorized access attempts.
4. VPN or SSH Tunneling
Consider using Virtual Private Network (VPN) or SSH tunneling for secure remote access. These technologies create an encrypted connection and provide an additional layer of protection for data transmission.
5. Regular Updates and Patch Management
Keep the NAS firmware, operating system, and any installed applications up to date with the latest security patches. Regularly check for updates and apply them promptly to fix vulnerabilities.
6. Intrusion Detection and Monitoring
Implement intrusion detection systems (IDS) and monitoring tools to detect any suspicious activities or unauthorized access attempts. Set up alerts or notifications to promptly respond to any security incidents.
7. Strong Password Policies
Enforce strong password policies with requirements for minimum length, complexity, and regular password changes. Educate remote users on the importance of using unique and secure passwords for NAS access.
8. Backup and Disaster Recovery
Regularly backup the data stored on the NAS and store the backups in a separate location. This ensures that even if the remote access is compromised or the NAS is attacked, important data can be restored.
By considering these security measures, remote access to a NAS can be made more secure, minimizing the risk of unauthorized access or data breaches.