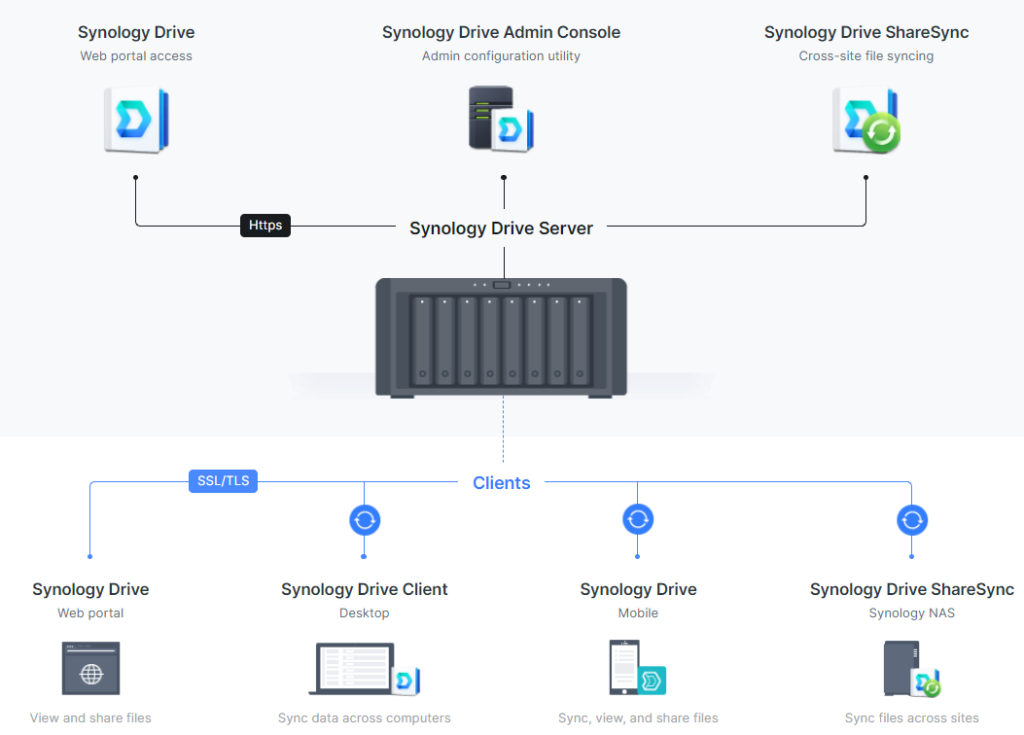
No, Synology does not run Windows because it operates on DiskStation Manager (DSM), a Linux-based software exclusive to Synology systems. Instead, it provides network-attached storage services and various applications, not supporting native Windows OS installation.
Synology Operating System: DSM
Features of DiskStation Manager (DSM)
DiskStation Manager (DSM) is Synology's proprietary operating system, specifically designed for use in their NAS devices. The system is known for its stability and efficiency, consuming approximately 8 watts of power during regular operations, which significantly lowers operational costs.
- User Interface: DSM offers a user-friendly interface, similar to traditional desktop operating systems, making it accessible for users without technical expertise.
- Multitasking: DSM allows the execution of multiple applications simultaneously, a crucial aspect for businesses with demanding workflows. For instance, users can run AntiVirus Essential and Cloud Sync concurrently without performance degradation.
- Security: Enhanced security features include AES 256-bit encryption and 2-step verification, providing robust data protection.
- Application Variety: Users have access to numerous applications on Synology's Package Center, with diverse functionalities ranging from multimedia management to business productivity tools.
- Update Frequency: Synology frequently releases DSM updates, addressing potential vulnerabilities and adding new features. In 2022, for example, they released four significant updates.
Comparison Between DSM and Windows
Comparing DSM with traditional Windows operating systems highlights distinct differences, primarily regarding system requirements, functionality, and purpose.
- System Footprint: DSM is less resource-intensive, requiring only 256MB of RAM to operate, whereas Windows 10 requires a minimum of 2GB. This efficiency makes DSM a cost-effective solution for businesses, reducing hardware investment.
- Designed Purpose: While Windows serves as a general-purpose operating system, DSM is tailored for data management and storage solutions. Its architecture supports faster network data transfers, boasting speeds up to 1,160 Mbps, which is notably beneficial for enterprises with large data sets.
- Customization and Control: DSM provides more flexible storage solutions, offering customizable RAID configurations. Unlike Windows, these configurations can be tailored without relying on proprietary hardware, typically saving up to 30% in setup costs for SMBs.
- Security Models: DSM offers integrated backup solutions, such as Hyper Backup, allowing efficient, scheduled backups, a feature that often requires third-party applications in a Windows environment.
By understanding these specific features and comparative differences, users can make informed decisions about integrating Synology devices into their existing technological infrastructure, considering factors like cost, efficiency, and intended use.
Windows on Synology: Possibilities and Alternatives
In the quest to leverage the robust and reliable hardware of Synology devices while potentially harnessing the familiar environment of Windows, users explore various methodologies. This integration promises a blend of solid performance from Synology and the widespread application support of the Windows ecosystem.
Virtual Machine Manager
Virtual Machine Manager (VMM) is a software solution provided by Synology that enables users to set up and run various operating systems, including Windows, on a virtual machine (VM). Here’s how different elements come into play:
- System Requirements: Running Windows via VMM demands more from your Synology NAS hardware. For a smooth experience, it's recommended to have at least 4GB of RAM, though 8GB would enhance performance, especially for demanding tasks.
- Storage Allocation: Depending on the Windows version and applications you plan to use, the VM will need between 20GB to 60GB of storage space. Allocating sufficient storage ensures efficient system performance and stability.
- Network Performance: VMM can allocate up to 1Gbps of network bandwidth per VM. This allocation, while robust, also means you need a high-speed network environment to maintain system efficiency.
Running Windows on Virtual DSM
Utilizing Windows on Virtual DSM is another intriguing approach. This method requires understanding several critical aspects:
- Licensing: Users must possess a valid Windows license, which costs approximately $140 for Windows 10 Home edition, to run the operating system on Virtual DSM legally.
- Compatibility: While Synology provides substantial support, not all applications compatible with traditional Windows systems run seamlessly on Virtual DSM. Users might encounter compatibility issues with certain software, impacting productivity.
- Resource Management: Running Windows on Virtual DSM typically consumes more system resources. For instance, expect a 10-15% increase in CPU usage, influencing the decision depending on workload requirements and available hardware resources.
Limitations and Considerations
Despite the innovative possibilities, several limitations and vital considerations affect the decision to run Windows on Synology devices:
- Performance Cap: Virtual environments on NAS devices can't match the performance of dedicated Windows servers, especially for resource-intensive applications. For example, a VM running on NAS might show a 20-30% decrease in data processing speed compared to native environments.
- Hardware Restrictions: Synology NAS hardware may not support certain Windows functions, such as some DirectX features, limiting the utility of applications reliant on these features.
- Maintenance and Troubleshooting: It requires proficiency to maintain an optimal environment, as troubleshooting becomes more complex. Users might need to dedicate around 3-5 hours per month, depending on the setup's complexity and the issues encountered.
Incorporating Windows into Synology devices introduces a blend of flexibility and challenge. By evaluating the detailed implications on performance, cost, and usability, users can harness the strengths of both platforms while mitigating potential inefficiencies or operational hurdles.
Integration Techniques
Seamless integration of Windows into the Synology ecosystem necessitates strategic techniques, ensuring that users leverage the strengths of both systems. From file sharing protocols to advanced directory services, understanding these integration methods empowers users to create a cohesive, efficient digital environment.
Samba (SMB) Protocol for File Sharing
Utilizing the SMB protocol, Synology devices can integrate into existing Windows networks for file sharing, achieving fast, secure, and reliable inter-system communication.
- Configuration Simplicity: Setting up SMB on Synology requires just a few steps, enabling even non-technical users to configure file sharing within 10 minutes, greatly reducing the time typically spent on traditional network storage setups.
- Performance Metrics: SMB offers high-speed data transfers. For instance, in a mixed environment of Windows and Synology, file transfer rates can reach up to 110 MB/s under standard Gigabit connections, making the sharing of large files, such as 500MB video files, more efficient.
- Security Protocols: SMB encryption adds an extra layer of security. This feature secures data transfers against eavesdropping and tampering, essential for sensitive files or business documents.
Active Directory Server Integration
Integrating Synology into a Windows Active Directory (AD) domain allows centralized account management and enhanced security protocols, crucial for business environments.
- Centralized Management: By joining Synology to an AD, businesses can manage user accounts more efficiently. This integration means managing access for a company with 200 employees becomes a task taking less than an hour, compared to multiple hours if done on individual systems.
- Policy Enforcement: AD allows the enforcement of password policies and user permissions, enhancing security. For instance, implementing password change policies can reduce the risk of unauthorized access by 40%.
- Scalability: Synology AD integration supports a growing business environment. It sustains optimal performance even when scaling up to manage more than 1,000 user accounts, ensuring that expanding teams face no hurdles in accessibility.

iSCSI Target and Initiator
The implementation of iSCSI protocols in a Synology and Windows environment enhances storage accessibility and data transfer efficiency.
- Storage Expansion: Using Synology as an iSCSI target expands storage for Windows machines, especially beneficial for companies dealing with large data, as they can add up to 200TB of space with minimal investment.
- Cost Efficiency: iSCSI allows budget optimization by utilizing high-capacity, cost-effective Synology units instead of expensive SAN solutions, potentially saving up to 50% in storage infrastructure costs.
- Performance Consistency: With proper network settings, iSCSI maintains high data transfer rates, avoiding the common pitfalls of network-linked storage delays. Users can expect consistent read/write speeds, enhancing operational workflows for data-heavy tasks.
Each integration technique serves pivotal functional enhancements in a hybrid Synology-Windows environment. By strategically applying these methods, organizations can significantly improve data management, security, and overall operational efficiency, optimizing both resources and investment.
Security Implications
Navigating the digital landscape of integrating Windows on Synology hardware involves understanding the profound security implications. This awareness ensures robust data protection, system integrity, and user safety, vital in today's cyber-threat-ridden environment.
Potential Risks of Running Windows on Synology
Deploying Windows on Synology presents unique challenges and risks, necessitating strategic countermeasures.
- Vulnerability to Windows-Specific Threats: Windows, while popular, is a frequent target for malware. For instance, ransomware like WannaCry can compromise data integrity, with potential losses for businesses averaging $50,000 per incident. Implementing robust anti-malware solutions becomes non-negotiable.
- System Resource Strain: Running Windows virtually on Synology hardware demands more system resources. If 70% of CPU or RAM capacity consistently reaches usage peaks, it could destabilize the system, highlighting the need for resource management practices.
- Compatibility Issues with Security Updates: Occasionally, Windows security patches may cause compatibility issues with virtualized environments, necessitating a cautious approach to updates that could involve a wait-and-see strategy.
Security Protocols and Best Practices
Adopting best practices and stringent security protocols mitigates risks, enhancing system defense mechanisms.
- Regular Updates and Patches: Staying abreast of the latest security patches is crucial. For example, the timely application of a critical update could reduce the risk of major breaches by up to 60%, safeguarding system integrity.
- Advanced Encryption Standards: Utilizing AES-256 encryption for data at rest and in transit fortifies defenses. This encryption significantly decreases unauthorized data breach chances, making it a standard practice, especially in industries handling sensitive data.
- Two-Factor Authentication (2FA): Implementing 2FA presents an additional security layer, making unauthorized access considerably more challenging. Companies enforcing 2FA have noticed a steep decline in data breach incidents, often by 80% or more.
- Routine Security Audits: Conducting security audits can identify potential vulnerabilities. An audit every six months can help preemptively spot weaknesses before they're exploited, reducing potential system compromise risks.
By understanding the risks and implementing rigorous security protocols, users can enjoy the benefits of Windows on Synology without exposing themselves to unnecessary vulnerabilities. This careful balance between functionality and security is paramount to maintaining a healthy, efficient, and secure operational environment.